Overview of Helix Authentication Service
The Helix Authentication Service (HAS) is designed to enable certain Perforce products to integrate with your organization's Identity Provider (IdP).
HAS supports:
- Two protocols: Security Assertion Markup Language (SAML) and OpenID Connect (OIDC).
- HAS can work with one IdP per protocol. For example, you might want to use OpenID Connect with Azure Active Directory, and SAML with Google G Suite IdP.
- Security-Enhanced Linux (SELinux) enabled in enforcing mode
The officially supported Example Identity Provider configurations include AuthO, Azur Active Directory, Okta (identity management), OneLogin, Google G Suite IdP for SAML. In addition, we have positive results with our initial testing with Shibboleth for SAML and Ping Identity. We expect HAS can also work with Cisco Duo Security and probably any standard IdP.
Helix Core and Helix ALM
After you perform the tasks of Installing Helix Authentication Service, Configuring Helix Authentication Service, and Starting Helix Authentication Service, you will go to one of the following:
- Next steps for Helix Core so you can to learn about the necessary work with a Helix Core Server Extension
- Next steps for Helix ALM so you can to learn about the necessary work with the Helix ALM License Server
Supported client applications and minimal versions
The client version must be equal to or greater than the version specified:
| Helix Core Client | Helix ALM or Surround SCM |
|---|---|
|
|
Sequence for Helix Core
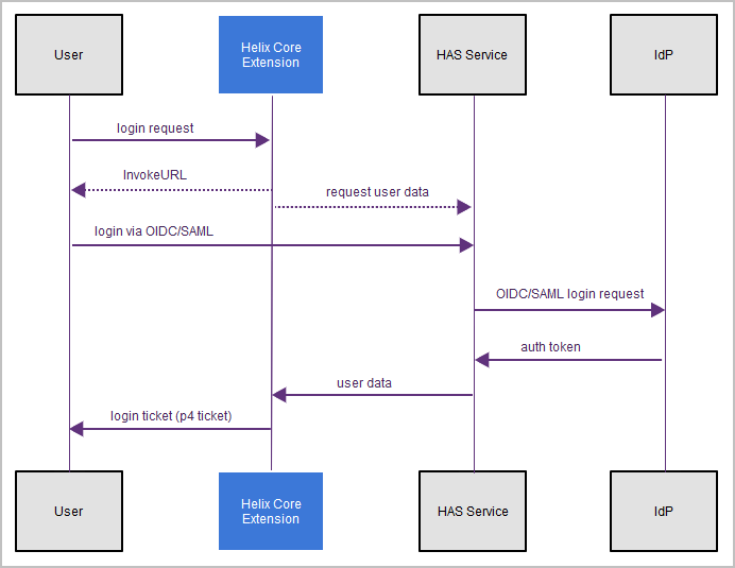
Helix Core clients get a p4 ticket to log in from a Helix Core Server Extension on the Helix Core server. To learn about the necessary work with a Helix Core Server Extension, see Next steps for Helix Core.
Sequence for Helix ALM
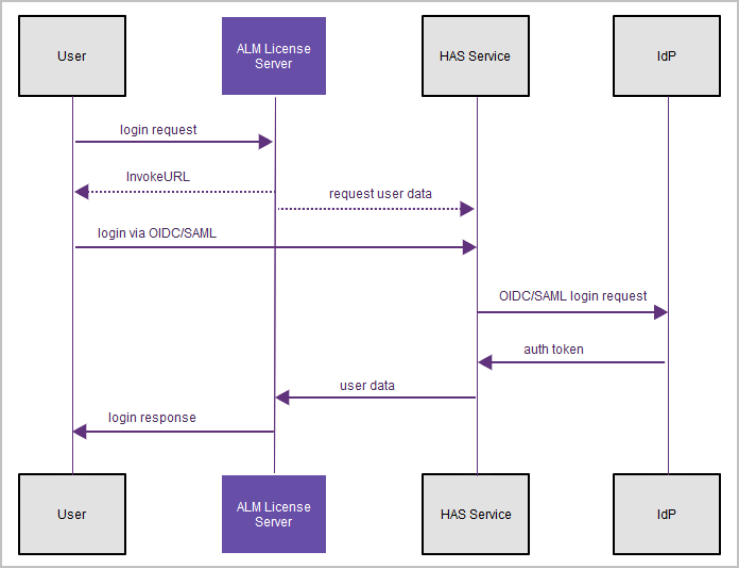
For Helix ALM clients, the user gets a login response from the Helix ALM License Server. See Next steps for Helix ALM.
Important security consideration
The IdP authentication precedes and is separate from the Helix Core "ticket" and the ALM License Server login reponse. Therefore, when the user logs out of Helix Core, the user is not necessarily logged out from the IdP's perspective.
Logging out of a Helix Core or Helix ALM client does not invoke a logout with the IdP. Depending on the IdP, subsequently starting a Helix Core or Helix ALM client might result with the user being logged in again without the user being prompted to provide credentials.
Load balancing
If you are using load balancing in front of HAS, configure your load balancer to:
- preserve session cookies so the login sequence can succeed
- use session affinity (sticky sessions) so that all requests from the client go to the same HAS instance